-
Laurent Modolo authoredLaurent Modolo authored
title: Text manipulation
author: "Laurent Modolo"
output:
rmdformats::downcute:
self_contain: true
use_bookdown: true
default_style: "light"
lightbox: true
css: "./www/style_Rmd.css"
if (!require("fontawesome")) {
install.packages("fontawesome")
}
if (!require("klippy")) {
install.packages("remotes")
remotes::install_github("rlesur/klippy")
}
library(fontawesome)
knitr::opts_chunk$set(echo = TRUE)
knitr::opts_chunk$set(comment = NA)
klippy::klippy(
position = c('top', 'right'),
color = "white",
tooltip_message = 'Click to copy',
tooltip_success = 'Copied !')
Ssh
Objective: Learn basics of ssh connection in GNU/Linux
In the previous section, we have seen how to run scripts and complex commands on your computer. In this session we are going to learn to do that over the network.
Most of the content from this session are from wikipedia.org
Network
First before talking about how to communicate over a network, we need to define what is a network in computational science. We can distinguish between two types of network, circuit switching networks and packet switching networks.
circuit switching
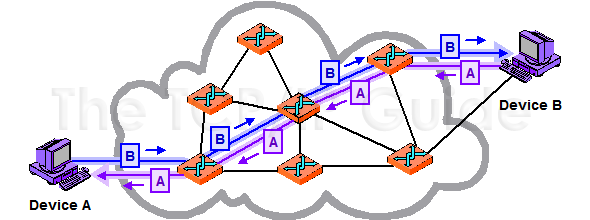
Circuit switching is the historical telephonic network architecture. When device A wants to communicate with device B, it has to establish a connection over the network. In a circuit switching network, the connections between a chain of nodes (hopefully the shortest chain) are established and fixed. Device A connects to the closest node and ask connection to Device B, this node will do the same thing to the closest node to Device B, so on and so forth until the connection reach Device B.
If you try to call someone, who is already in a phone conversation, the line will be occupied.
packet switching
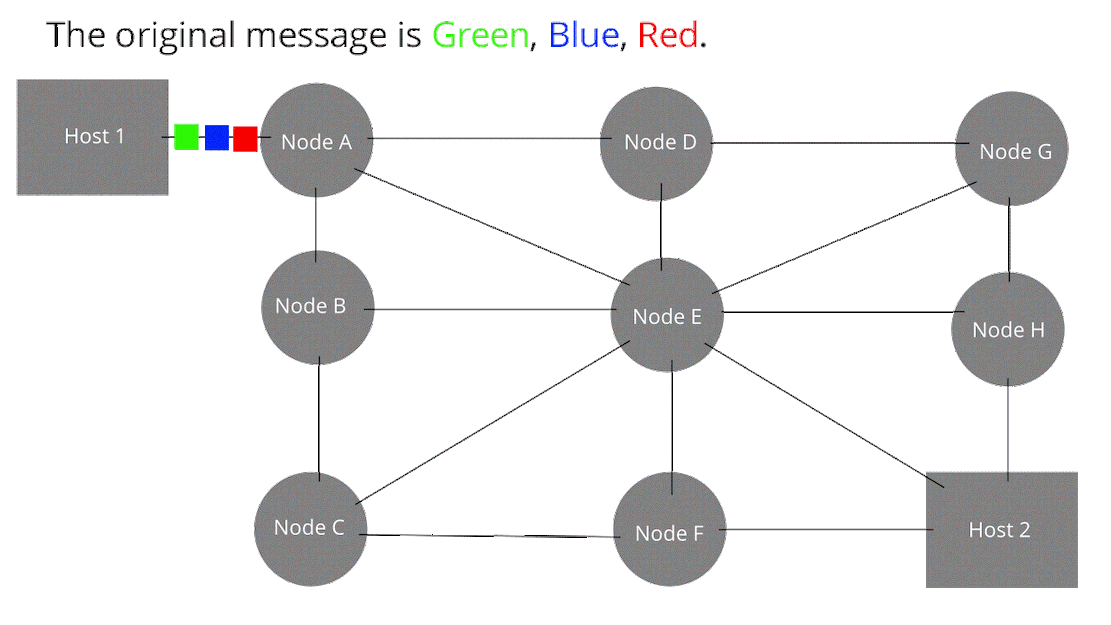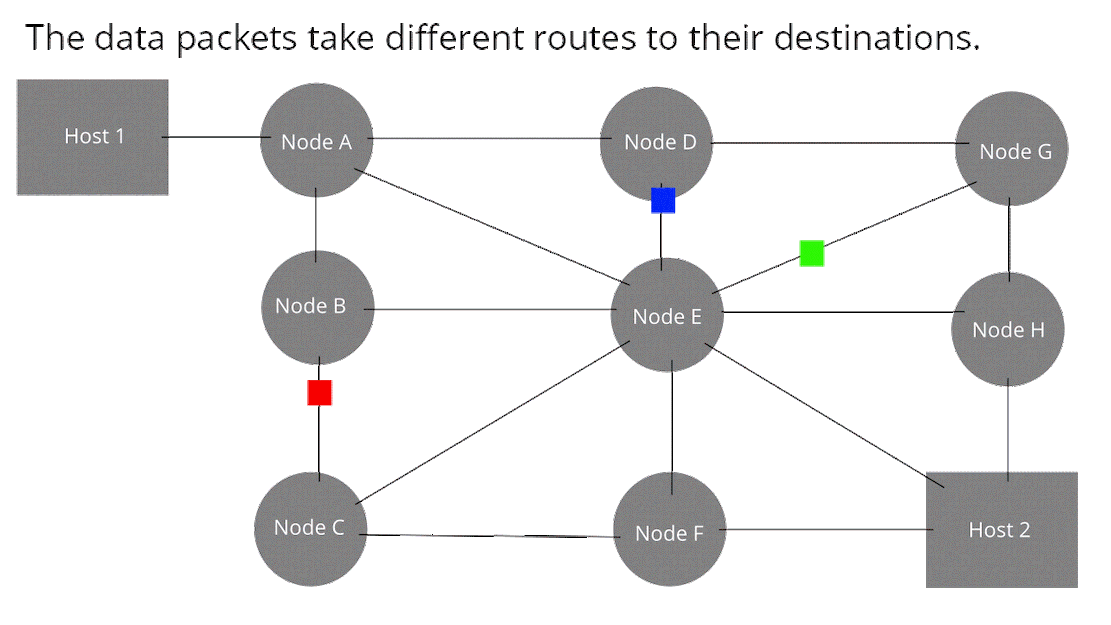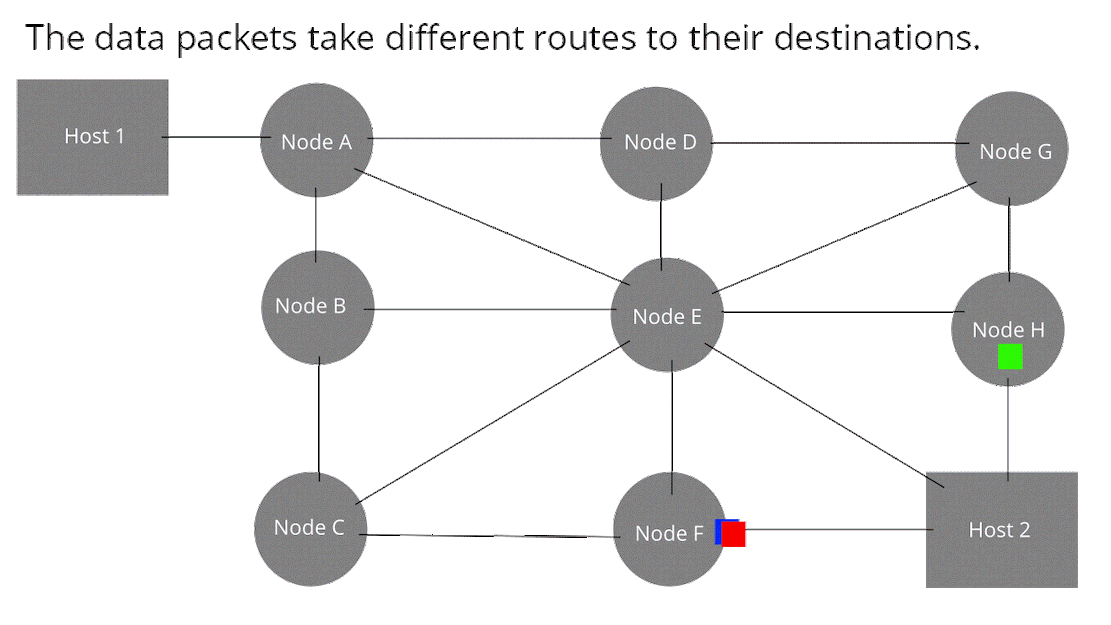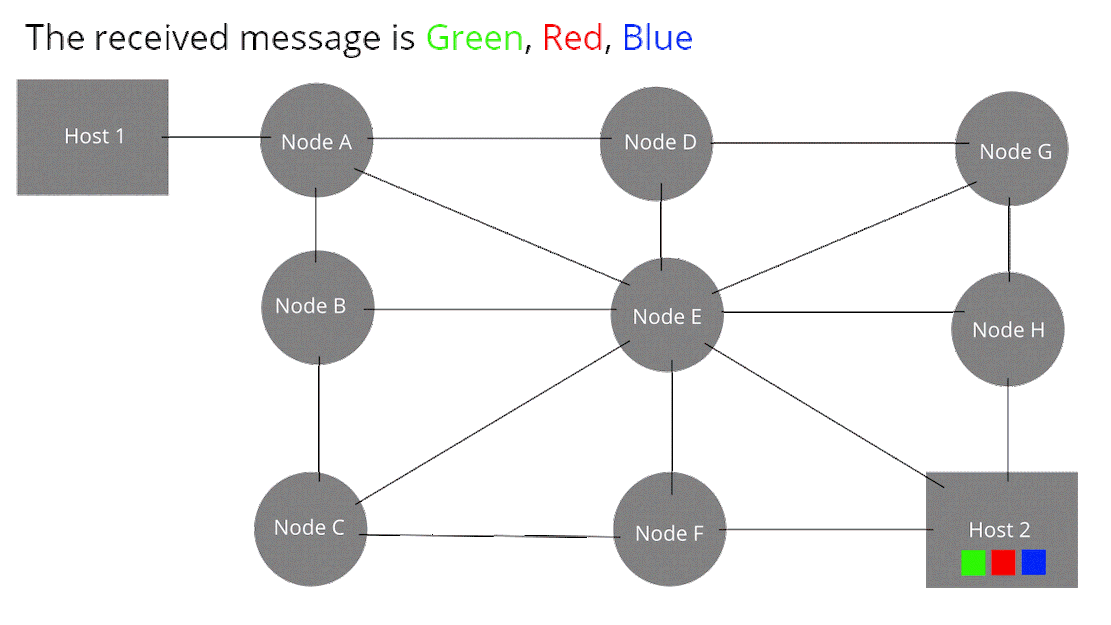
Packet switching is a method of grouping data over the network into packets. Each packet has a header and a payload. The header data can be read by each node to direct the packet to its destination. The header data also inform the Host 2 of the packets order. The payload contains the data that we want to transmit over the network. In packet switching, the network bandwidth is not pre-allocated like in circuit switching. Each packet is called a datagram.
“A self-contained, independent entity of data carrying sufficient information to be routed from the source to the destination computer without reliance on earlier exchanges between this source and destination computer and the transporting network.”
In a packet switching network when you send a flux of data (video, sound, etc.), you have the illusion of continuity like for process switching handled by the scheduler.
Internet Protocol (IP)
The Internet Protocol (IP) is the principal communications protocol in the Internet protocol suite for relaying datagrams across network boundaries. Its routing function enables internetworking, and essentially establishes the Internet.
IP has the task of delivering packets from the source host to the destination host solely based on the IP addresses in the packet headers. For this purpose, IP defines packet structures that encapsulate the data to be delivered. It also defines addressing methods.
The first major version of IP, Internet Protocol Version 4 (IPv4), is the dominant protocol of the Internet. Its successor is Internet Protocol Version 6 (IPv6), which has been in increasing deployment on the public Internet since c. 2006.
IPv4
An IPv4 is composed of 4 digits ranging from 0 to 255 separated by . , which gives an address space of 4294967296 (2^32) addresses. Some combinations of IPv4 are restricted:
| Address block | Address range | Number of addresses | Scope | Description |
|---|---|---|---|---|
| 0.0.0.0/8 | 0.0.0.0–0.255.255.255 | 16777216 | Software | Current network[6] (only valid as source address). |
| 10.0.0.0/8 | 10.0.0.0–10.255.255.255 | 16777216 | Private network | Used for local communications within a private network.[7] |
| 100.64.0.0/10 | 100.64.0.0–100.127.255.255 | 4194304 | Private network | Shared address space[8] for communications between a service provider and its subscribers when using a carrier-grade NAT. |
| 127.0.0.0/8 | 127.0.0.0–127.255.255.255 | 16777216 | Host | Used for loopback addresses to the local host.[6] |
| 169.254.0.0/16 | 169.254.0.0–169.254.255.255 | 65536 | Subnet | Used for link-local addresses[9] between two hosts on a single link when no IP address is otherwise specified, such as would have normally been retrieved from a DHCP server. |
| 172.16.0.0/12 | 172.16.0.0–172.31.255.255 | 1048576 | Private network | Used for local communications within a private network.[7] |
| 192.0.0.0/24 | 192.0.0.0–192.0.0.255 | 256 | Private network | IETF Protocol Assignments.[6] |
| 192.0.2.0/24 | 192.0.2.0–192.0.2.255 | 256 | Documentation | Assigned as TEST-NET-1, documentation and examples.[10] |
| 192.88.99.0/24 | 192.88.99.0–192.88.99.255 | 256 | Internet | Reserved.[11] Formerly used for IPv6 to IPv4 relay[12] (included IPv6 address block 2002::/16). |
| 192.168.0.0/16 | 192.168.0.0–192.168.255.255 | 65536 | Private network | Used for local communications within a private network.[7] |
| 198.18.0.0/15 | 198.18.0.0–198.19.255.255 | 131072 | Private network | Used for benchmark testing of inter-network communications between two separate subnets.[13] |
| 198.51.100.0/24 | 198.51.100.0–198.51.100.255 | 256 | Documentation | Assigned as TEST-NET-2, documentation and examples.[10] |
| 203.0.113.0/24 | 203.0.113.0–203.0.113.255 | 256 | Documentation | Assigned as TEST-NET-3, documentation and examples.[10] |
| 224.0.0.0/4 | 224.0.0.0–239.255.255.255 | 268435456 | Internet | In use for IP multicast.[14] (Former Class D network). |
| 240.0.0.0/4 | 240.0.0.0–255.255.255.254 | 268435455 | Internet | Reserved for future use.[15] (Former Class E network). |
| 255.255.255.255/32 | 255.255.255.255 | 1 | Subnet | Reserved for the "limited broadcast" destination address.[6][16] |
IPv6
An IPv6 is composed of 8 groups of 4 digits long number separated by :. The numbers are in hexadecimal format (number of base 16, randing from 0 to 9 and A to F). Compared to IPv4, IPv6 allows for 2^128 = 340,282,366,920,938,463,463,374,607,431,768,211,456 addresses (approximately 3.4×10^38). For example, an IP address is: 2001:0db8:0000:0000:0000:ff00:0042:8329
To display your VM IP addresses you can use the following command: ip address show
Local IPv6 addresses start with fe80::
Domain Name System (DNS)
Instead of using IP addresses in your everyday life, you often use the domain name. The DNS is composed of many DNS servers that are hierarchically organized and decentralized. By querying the DNS with a particular domain name, the correct name server will return the corresponding IP address. For most network tools, you can use domain names (URL) or IP addresses.
Transmission Control Protocol (TCP)
The Transmission Control Protocol (TCP) is one of the main protocols of the Internet protocol suite. TCP provide, reliable, ordered, and error-checked delivery of a stream of data between applications running on hosts communincating over an IP network.
- data arrives in-order
- data has minimal error (i.e., correctness)
- duplicate data is discarded
- lost or discarded packets are resent
- includes traffic congestion control
- Heavtweight (no ordering of messages, no tracking connections, etc. It is a very simple transport layer designed on top of IP)
User Datagram Protocol (UDP)
UDP uses a simple connectionless communication model with a minimum of protocol mechanisms.
- Unreliable
- Not ordered
- Broadcast (being connectionless, UDP can broadcast - sent packets can be addressed to be receivable by all devices on the subnet)
- Multicast (a single datagram packet can be automatically routed without duplication to a group of subscribers)
- Lightweight (no ordering of messages, no tracking connections, etc. It is a very simple transport layer designed on top of IP)
Port
Higher, communication protocols like TCP and UDP, also define port. A port is a communication endpoint. When software wants to communicate overt TCP or UDP it will do so using a specific port. Each system has port numbers ranging from 0 to 65535. Port numbered from 0 through 1023 are system ports used by well-known processes (you need specific rights to use them).
Here are a list of notable port numbers:
| Number | Assignment |
|---|---|
| 20 | File Transfer Protocol (FTP) Data Transfer |
| 21 | File Transfer Protocol (FTP) Command Control |
| 22 | Secure Shell (SSH) Secure Login |
| 23 | Telnet remote login service, unencrypted text messages |
| 25 | Simple Mail Transfer Protocol (SMTP) E-mail routing |
| 53 | Domain Name System (DNS) service |
| 67, 68 | Dynamic Host Configuration Protocol (DHCP) |
| 80 | Hypertext Transfer Protocol (HTTP) used in the World Wide Web |
| 110 | Post Office Protocol (POP3) |
| 119 | Network News Transfer Protocol (NNTP) |
| 123 | Network Time Protocol (NTP) |
| 143 | Internet Message Access Protocol (IMAP) Management of digital mail |
| 161 | Simple Network Management Protocol (SNMP) |
| 194 | Internet Relay Chat (IRC) |
| 443 | HTTP Secure (HTTPS) HTTP over TLS/SSL |
Nowadays, ports provide multiplexing, which means that multiple service or communication session can use the same port number.
SSH
There are numerous other protocols (RTP for example). But most of them run over the TCP and UDP protocols. SSH or Secure Shell is one of them. SSH is a cryptographic network protocol for operating network services securely over an unsecured network.
SSH use a client-server architecture, you use an SSH client to connect to an SSH server. By default most Linux distribution don’t comes with an SSH server installed. For the IFB, SSH connection is the default way to connect to your VMs, so you should have an SSH sever up and running.
Find the name of the SSH server process
Solution
```sh ps -el | grep "ssh" ```
SSH uses Public-key cryptography (or asymmetric cryptography), to secure it’s communications.